To be safe, the internet needs reliable encryption. But the standards, software and hardware it uses are vulnerable
INTELLIGENCE agencies exist to steal secrets, and necessarily break other countries’ laws to do so. Much of the brouhaha around the disclosures by Edward Snowden, a fugitive systems administrator from America’s National Security Agency now living in Russia, misses that fact. But his latest leaks, published on September 5th in Britain’s Guardian and other outlets, highlight another aspect of the NSA’s work.
Purportedly, the NSA, with its British counterpart GCHQ, is trying not just to break the codes that allow private communication over the internet, but is sabotaging them. The tactics allegedly include undermining official standards bodies, and suborning big IT companies—if necessary, by infiltrating them. The aim is to insert “backdoors”: hidden flaws that help outsiders to eavesdrop. And the New York Times quotes a GCHQ document which says the NSA has “led an aggressive, multipronged effort to break widely used internetencryption technologies”. “Vast amounts” of encrypted data which used to be discarded are now “exploitable”.
This is big news, if true. For most of history, cryptography was an arcane discipline, of interest only to mathematicians and to some parts of government, just as the internet was once an academic research network that paid little attention to security. Now encryption of electronic data is an essential part of modern life. It secures the financial networks that link the world’s banks, protects credit cards, stops mobile-phone calls from being listened to, guards medical records and lawyers’ letters to their clients. Though cybercrime is a growing menace, reliable encryption remains the foundation on which the trillion-dollar edifice of e-commerce is built: without it, nobody would be able safely to make a payment online. For critics, sabotaging such codes is akin to a government secretly commanding lockmakers to make their products easier to pick—and to do so amid an epidemic of burglary.
Researchers, civil libertarians and conspiracy theorists have long suspected that policemen and spies would take steps to hamper individuals’ access to the uncrackably strong codes that modern computers can create. These bring privacy—but give great scope to villains. In the 1990s America classed cryptography as a weapon, and let only weakened versions of it be sold abroad. Western spies were rumoured to have installed “backdoors” into equipment sold by Crypto, a Swiss firm which exported to the Libyan and Iranian governments (the firm denied it). Some export versions of Lotus Notes, a rival to Microsoft’s Office suite of software, came with weakened secrecy. In 1999 researchers unearthed signing software suspiciously entitled “_NSAKEY” in some versions of Microsoft Windows (the company denied that it was a backdoor).
But outsiders have mostly relied on guesswork. After the latest revelations experts are scrambling to work out what the spies might have done, which encryption is affected and what will happen next. Intriguingly, Mr Snowden himself has said that “properly implemented strong crypto systems are one of the few things that you can rely on”. The question is what he means by “properly implemented”.
“Before this happened, wondering about government backdoors had the whiff of conspiracy theory,” says Matthew Green, of Johns Hopkins University, in Maryland. “But now it’s the exact opposite…Everything is suspect.” People are wondering where backdoors do not exist, rather than where they do. Mr Green sees three kinds of possible attack: on cryptographic standards, on software and on hardware.
Your keys, please
In theory, standards should be the hardest to subvert. They define the maths and techniques that encryption schemes use. They are poked and prodded by both academic cryptographers and government agencies (including the NSA itself, in its advisory role) to ensure that they are strong.
But the agency has made some strange-looking recommendations over the years. Cryptography depends on random numbers. These are hard for computers, which are decidedly non-random machines, to generate. Making random-number generators less random would be a fine, and subtle, way to undermine secrecy. In 2006 the NSA supported a random-number generator that was 1,000 times slower than its closest competitor. Researchers later found a problem which could badly weaken any encryption that relied on it.
Cryptography also depends on so-called “trapdoor functions”, bits of mathematics that are easy to do in one direction but virtually impossible to reverse. One common method is based on the assumed difficulty of finding the prime factors of enormous numbers. But the NSA (and many security researchers) have also been touting new codes based on a different sort of mathematics involving elliptic curves. This encryption should be stronger and less computationally taxing. But its equations require some constants. Bruce Schneier, a cryptographer and security commentator, frets that the NSA may have picked those constants so as to make the resulting codes vulnerable to decryption. He has no proof, he stresses, but “I think it’s a good guess that the NSA knows something about elliptic curves that we don’t. So I don’t trust them.” (Mr Schneier has seen many of Mr Snowden’s source documents but says his suspicions do not arise from studying them. He did not discuss them with The Economist.)
Software should be slightly easier to sabotage. One of the most commonly used cryptographic suites on the internet is written by Microsoft. Other leaks indicate that the firm has been subject to considerable legal pressure from American intelligence. Its code is “closed-source”, meaning that it is hard for outsiders to see how the programs work. “Open-source” software—where code is open for anyone to inspect—abounds, and should offer a bit more security. But flaws crop up there too. A random-number generator in Debian, a version of the open-source Linux operating system, had been misfiring for nearly two years before it was spotted in 2008. How many such bugs are accidental?
Dodgy hardware is even harder to find. The routers and switches that marshal traffic around the internet are largely designed by American firms; bugs infest them as well (a big one was found in 2011). Chips themselves have millions of transistors and complex embedded software. Inspecting one thoroughly is immensely difficult and costly. Intel, the world’s biggest chipmaker, builds a random-number generator into its products. Steve Blank, a Silicon Valley veteran, has publicly wondered whether America’s spies might have modified those chips (with or without Intel’s knowledge) to make the numbers less random. Intel says: “We do not include backdoors or any other unauthorised access to our products.”
But what once seemed paranoia is now a growing worry. Mr Schneier’s guess is that “the odds are almost zero that the NSA hasn’t tried to influence Intel’s chips.” In 2012 a paper from two British researchers described an apparent backdoor burned into a chip designed by an American firm called Actel and manufactured in China. The chip is widely used in military and industrial applications. Actel says the feature is innocent: a tool to help its engineers fix hardware bugs.
Who cares?
The NSA and its allies see things differently. For intelligence professionals, the efforts to compromise commercial products are a tempest in a teapot. Time was when the nation’s adversaries used military and diplomatic codes. Now they use private ones, too. So, they say, the NSA naturally must change the focus of its work, just as it now must target individual terrorists as well as foreign leaders. Are the critics really saying that the NSA must give up its work (or publicise its methods, rendering them useless)? Polls suggest a narrow majority of Americans, at least, prefer safety.
Moreover, aver the NSA’s defenders, the idea that commercial cryptography is now useless is false. The software and hardware is still robust enough to protect the integrity of communications for most uses. Only someone with oodles of skill and computing power can break it. That is well beyond the abilities of cyber-criminals. Even if they stumble across one or two security flaws, they will not have the ability to exploit them. If the NSA or allied agencies need a subtle way to access the material they need at a moment’s notice, that is useful, not scandalous.
Civil libertarians are unconvinced. They want to live in a world in which secure communication is at least theoretically possible. Less high-minded types worry, too. Security researchers dislike backdoors because they could be useful not just to their architects, but to malefactors. If the main protection against this is obscurity, then given the numbers of enthusiasts, crooks and spies who poke around other people’s computer systems, it may prove flimsy. (For other countermeasures, see article.) If the cryptography that secures e-commerce or banking has a built-in vulnerability, and a rogue outsider discovers it, the consequences could be catastrophic. Mr Snowden’s leaks will have brought more hunters to that quest.
Some companies will gain from the latest disclosures. “The unintended consequence of all this is that we are about to enter the next great wave of cryptographic research,” says Matthew Prince of CloudFlare, which makes products to speed up and protect websites. Wickr, an American outfit that makes a highly secure messaging app, is one of those already profiting from the panic. “Our downloads have grown tremendously since the NSA revelations,” says Nico Sell, a co-founder.
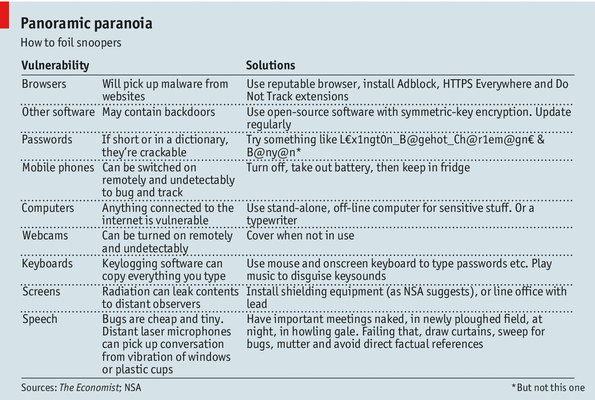
But overall, the damage seems likely to far outweigh the benefits. America’s public image has taken a pounding: its courts, laws and politicians seem unable to supervise the spooks properly. Whistleblowers—supposedly cherished by the Obama administration—are persecuted, not vindicated. The NSA, a recent leak suggests, is spying not just on foreign adversaries, but also American companies’ commercial rivals, something that foreign firms and governments have worried about for years. James Clapper, the director of national intelligence, faces an uphill struggle in his argument that America spies on business communications, but only to give early warning of financial crises and the like, not to give American firms a boost. Even those who mistrust Mr Snowden and his allies, who contest the inferences drawn from the leaks, and defend the role of the NSA, acknowledge the harm done by the supposedly super-secret agency’s inability to keep its own systems secure.
The most immediate damage is to America’s leading technology firms. They were already battling to contain the damage caused by previous allegations of how the NSA hoovered up their customers’ data. Protectionists can now pose as champions of privacy and national dignity. German politicians have urged people to shun American web firms if they want to keep their data secure. The Indian government is reportedly considering a ban on the use of Google’s Gmail service for sending official communications. And tech firms in places like Switzerland have seen a spike in inquiries from companies looking for a haven for their data.
Some experts play this down. It would be naive to think that the NSA did not have such capabilities. Lawrence Pingree of Gartner, a research firm, says some American “cloud computing” firms, which store and help manage other firms’ data, could see a dip in business, but he reckons the overall impact will be “minimal”.
But a report by the Information Technology and Innovation Foundation, a think-tank, estimates the leaks could cost that industry $22 billion-35 billion in lost revenues between now and 2016. Some customers may shun technology with any American connection. Some may have to because their governments pass laws mandating the use of local cloud operators for certain kinds of data.
American telecoms-equipment makers such as Cisco could also lose business abroad to foreign rivals—not least to Huawei, a controversial Chinese rival. Concerns about possible ties to Chinese espionage (which it denies) have hampered its expansion in America. William Plummer, its spokesman, says the industry should work together to secure networks and data, while putting “political games and distracting country-of-origin shenanigans behind us”.
But America’s big consumer internet firms, with their global horizons, have the most to lose. On September 9th several of them, including Google and Yahoo, filed new or revised lawsuits with America’s Foreign Intelligence Surveillance Court requesting permission to reveal more detailed information about the kinds of requests they receive from American government agencies. Both firms made clear in their suits that their inability to respond to misleading surveillance-related stories with specific data about such requests had harmed their reputation and their business, though they did not put a figure on the damage done.
Now America’s tech giants stand accused not just of mishandling their customers’ data, but, in effect, of knowingly selling them flawed software. Microsoft has always denied installing backdoors. It says it has “significant concerns” about the latest leaks and will be “pressing the government for an explanation”.
The damage goes well beyond individual companies’ brands. American technology executives often use their economic clout to shape global standards in ways that suit their companies. Now that will be harder. American input to international cryptographic standards, for example, will have to overcome sceptical scrutiny: are these suggestions honest, or do they have a hidden agenda? More broadly still, America has spent years battling countries such as Russia, China and Iran which want to wrest control of the internet from the mainly American engineers and companies who run it now, and give a greater role to governments. America has fought them off, claiming that its influence keeps the internet open and free.
Now a balkanisation of the web seems more likely. Jason Healey of the Atlantic Council, a think-tank, says that the denizens of Washington, DC, have lost sight of the fact that the true source of American cyber-power is neither the NSA and its code-breaking prowess nor the offensive capabilities that produced the Stuxnet virus, which hit centrifuges at an Iranian nuclear plant; it is the hugely successful firms which dominate cyberspace and help disseminate American culture and values worldwide. By tarnishing the reputations of these firms, America’s national-security apparatus has scored an own goal.
fecha |
Título |
23/09/2023| |
|
06/09/2022| |
|
17/09/2020| |
|
15/09/2020| |
|
18/08/2020| |
|
05/07/2020| |
|
01/06/2020| |
|
30/05/2020| |
|
15/05/2020| |
|
26/04/2020| |
|
14/04/2020| |
|
04/04/2020| |
|
24/03/2020| |
|
19/01/2020| |
|
23/08/2019| |
|
22/08/2019| |
|
20/08/2019| |
|
21/07/2019| |
|
04/02/2019| |
|
13/01/2019| |
|
26/12/2018| |
|
24/12/2018| |
|
04/10/2018| |
|
13/08/2018| |
|
12/08/2018| |
|
07/08/2018| |
|
03/08/2018| |
|
28/07/2018| |
|
25/07/2018| |
|
23/07/2018| |
|
23/07/2018| |
|
21/07/2018| |
|
01/07/2018| |
|
12/06/2018| |
|
26/04/2018| |
|
22/04/2018| |
|
10/04/2018| |
|
24/03/2018| |
|
20/03/2018| |
|
04/03/2018| |
|
03/02/2018| |
|
11/12/2017| |
|
11/12/2017| |
|
11/12/2017| |
|
02/12/2017| |
|
17/11/2017| |
|
16/11/2017| |
|
07/11/2017| |
|
01/11/2017| |
|
28/10/2017| |
|
26/10/2017| |
|
05/10/2017| |
|
26/09/2017| |
|
09/09/2017| |
|
20/08/2017| |
|
19/08/2017| |
|
14/08/2017| |
|
01/08/2017| |
|
22/07/2017| |
|
20/07/2017| |
|
15/07/2017| |
|
09/07/2017| |
|
07/07/2017| |
|
12/06/2017| |
|
10/06/2017| |
|
13/05/2017| |
|
13/05/2017| |
|
30/04/2017| |
|
19/04/2017| |
|
18/04/2017| |
|
04/04/2017| |
|
28/03/2017| |
|
28/03/2017| |
|
17/03/2017| |
|
12/03/2017| |
|
05/03/2017| |
|
05/03/2017| |
|
24/02/2017| |
|
24/02/2017| |
|
22/02/2017| |
|
22/02/2017| |
|
20/02/2017| |
|
01/02/2017| |
|
16/01/2017| |
|
16/01/2017| |
|
15/01/2017| |
|
10/01/2017| |
|
01/01/2017| |
|
24/11/2016| |
|
20/11/2016| |
|
11/11/2016| |
|
24/10/2016| |
|
17/10/2016| |
|
15/10/2016| |
|
14/10/2016| |
|
14/10/2016| |
|
13/10/2016| |
|
10/10/2016| |
|
01/10/2016| |
|
14/09/2016| |
|
09/09/2016| |
|
04/09/2016| |
|
04/09/2016| |
|
17/08/2016| |
|
14/08/2016| |
|
14/08/2016| |
|
16/06/2016| |
|
11/06/2016| |
|
06/06/2016| |
|
06/06/2016| |
|
27/05/2016| |
|
07/05/2016| |
|
14/04/2016| |
|
14/04/2016| |
|
11/04/2016| |
|
11/04/2016| |
|
25/03/2016| |
|
18/03/2016| |
|
18/03/2016| |
|
18/03/2016| |
|
15/03/2016| |
|
15/03/2016| |
|
13/03/2016| |
|
08/02/2016| |
|
07/02/2016| |
|
24/01/2016| |
|
05/01/2016| |
|
04/01/2016| |
|
31/12/2015| |
|
16/12/2015| |
|
16/12/2015| |
|
11/12/2015| |
|
28/11/2015| |
|
21/11/2015| |
|
10/11/2015| |
|
07/11/2015| |
|
03/11/2015| |
|
31/10/2015| |
|
19/10/2015| |
|
19/10/2015| |
|
15/10/2015| |
|
28/09/2015| |
|
20/09/2015| |
|
18/09/2015| |
|
03/09/2015| |
|
31/08/2015| |
|
28/08/2015| |
|
21/08/2015| |
|
16/08/2015| |
|
08/08/2015| |
|
08/08/2015| |
|
30/07/2015| |
|
30/07/2015| |
|
22/07/2015| |
|
27/06/2015| |
|
27/06/2015| |
|
17/06/2015| |
|
09/06/2015| |
|
06/06/2015| |
|
03/06/2015| |
|
30/05/2015| |
|
30/05/2015| |
|
22/05/2015| |
|
21/05/2015| |
|
19/05/2015| |
|
06/05/2015| |
|
02/05/2015| |
|
03/04/2015| |
|
31/03/2015| |
|
29/03/2015| |
|
09/03/2015| |
|
04/03/2015| |
|
25/02/2015| |
|
19/02/2015| |
|
16/02/2015| |
|
16/02/2015| |
|
01/02/2015| |
|
01/02/2015| |
|
27/01/2015| |
|
27/01/2015| |
|
27/01/2015| |
|
23/01/2015| |
|
22/01/2015| |
|
13/01/2015| |
|
13/01/2015| |
|
02/01/2015| |
|
02/01/2015| |
|
22/12/2014| |
|
21/12/2014| |
|
21/12/2014| |
|
18/12/2014| |
|
14/12/2014| |
|
04/12/2014| |
|
01/12/2014| |
|
01/12/2014| |
|
28/11/2014| |
|
20/11/2014| |
|
20/11/2014| |
|
12/11/2014| |
|
01/11/2014| |
|
21/10/2014| |
|
19/10/2014| |
|
18/10/2014| |
|
14/10/2014| |
|
12/10/2014| |
|
12/10/2014| |
|
12/10/2014| |
|
10/10/2014| |
|
06/10/2014| |
|
06/10/2014| |
|
01/10/2014| |
|
29/09/2014| |
|
29/09/2014| |
|
19/09/2014| |
|
15/09/2014| |
|
09/09/2014| |
|
01/09/2014| |
|
26/08/2014| |
|
26/08/2014| |
|
19/08/2014| |
|
19/08/2014| |
|
08/08/2014| |
|
29/07/2014| |
|
29/07/2014| |
|
27/07/2014| |
|
27/07/2014| |
|
21/07/2014| |
|
21/07/2014| |
|
21/07/2014| |
|
03/07/2014| |
|
01/07/2014| |
|
23/06/2014| |
|
21/06/2014| |
|
18/06/2014| |
|
18/06/2014| |
|
18/06/2014| |
|
29/05/2014| |
|
21/05/2014| |
|
17/05/2014| |
|
09/05/2014| |
|
09/05/2014| |
|
09/05/2014| |
|
05/05/2014| |
|
27/04/2014| |
|
20/04/2014| |
|
20/04/2014| |
|
20/04/2014| |
|
11/04/2014| |
|
07/04/2014| |
|
31/03/2014| |
|
31/03/2014| |
|
25/03/2014| |
|
04/03/2014| |
|
27/02/2014| |
|
21/02/2014| |
|
17/02/2014| |
|
14/02/2014| |
|
04/02/2014| |
|
31/01/2014| |
|
31/01/2014| |
|
25/01/2014| |
|
16/01/2014| |
|
15/01/2014| |
|
15/01/2014| |
|
14/01/2014| |
|
02/01/2014| |
|
25/12/2013| |
|
19/12/2013| |
|
11/12/2013| |
|
11/12/2013| |
|
06/12/2013| |
|
03/12/2013| |
|
03/12/2013| |
|
27/11/2013| |
|
25/11/2013| |
|
20/11/2013| |
|
17/11/2013| |
|
11/11/2013| |
|
08/11/2013| |
|
06/11/2013| |
|
05/11/2013| |
|
28/10/2013| |
|
28/10/2013| |
|
28/10/2013| |
|
27/10/2013| |
|
21/10/2013| |
|
21/10/2013| |
|
21/10/2013| |
|
16/10/2013| |
|
10/10/2013| |
|
09/10/2013| |
|
09/10/2013| |
|
29/09/2013| |
|
21/09/2013| |
|
17/09/2013| |
|
15/09/2013| |
|
15/09/2013| |
|
14/09/2013| |
|
03/09/2013| |
|
27/08/2013| |
|
27/08/2013| |
|
17/08/2013| |
|
12/08/2013| |
|
12/08/2013| |
|
12/08/2013| |
|
07/08/2013| |
|
29/07/2013| |
|
18/07/2013| |
|
18/07/2013| |
|
12/07/2013| |
|
12/07/2013| |
|
11/07/2013| |
|
07/07/2013| |
|
06/07/2013| |
|
29/06/2013| |
|
21/06/2013| |
|
21/06/2013| |
|
16/06/2013| |
|
16/06/2013| |
|
16/06/2013| |
|
12/06/2013| |
|
03/06/2013| |
|
03/06/2013| |
|
30/05/2013| |
|
30/05/2013| |
|
28/05/2013| |
|
28/05/2013| |
|
28/05/2013| |
|
23/05/2013| |
|
23/05/2013| |
|
20/05/2013| |
|
20/05/2013| |
|
16/05/2013| |
|
16/05/2013| |
|
10/05/2013| |
|
10/05/2013| |
|
06/05/2013| |
|
04/05/2013| |
|
23/04/2013| |
|
21/04/2013| |
|
21/04/2013| |
|
19/04/2013| |
|
14/04/2013| |
|
11/04/2013| |
|
08/04/2013| |
|
03/04/2013| |
|
31/03/2013| |
|
22/03/2013| |
|
21/03/2013| |
|
14/03/2013| |
|
14/03/2013| |
|
11/03/2013| |
|
11/03/2013| |
|
11/03/2013| |
|
03/03/2013| |
|
03/03/2013| |
|
03/03/2013| |
|
03/03/2013| |
|
03/03/2013| |
|
25/02/2013| |
|
25/02/2013| |
|
18/02/2013| |
|
18/02/2013| |
|
18/02/2013| |
|
14/02/2013| |
|
14/02/2013| |
|
11/02/2013| |
|
11/02/2013| |
|
11/02/2013| |
|
27/01/2013| |
|
25/01/2013| |
|
22/01/2013| |
|
22/01/2013| |
|
15/01/2013| |
|
13/01/2013| |
|
10/01/2013| |
|
10/01/2013| |
|
10/01/2013| |
|
09/01/2013| |
|
09/01/2013| |
|
30/12/2012| |
|
25/12/2012| |
|
25/12/2012| |
|
24/12/2012| |
|
24/12/2012| |
|
19/12/2012| |
|
18/12/2012| |
|
18/12/2012| |
|
12/12/2012| |
|
08/12/2012| |
|
06/12/2012| |
|
05/12/2012| |
|
04/12/2012| |
|
04/12/2012| |
|
27/11/2012| |
|
26/11/2012| |
|
24/11/2012| |
|
24/11/2012| |
|
24/11/2012| |
|
19/11/2012| |
|
18/11/2012| |
|
18/11/2012| |
|
18/11/2012| |
|
10/11/2012| |
|
09/11/2012| |
|
09/11/2012| |
|
09/11/2012| |
|
07/11/2012| |
|
07/11/2012| |
|
07/11/2012| |
|
07/11/2012| |
|
07/11/2012| |
|
07/11/2012| |
|
05/11/2012| |
|
02/11/2012| |
|
02/11/2012| |
|
01/11/2012| |
|
31/10/2012| |
|
31/10/2012| |
|
30/10/2012| |
|
30/10/2012| |
|
26/10/2012| |
|
26/10/2012| |
|
26/10/2012| |
|
26/10/2012| |
|
19/10/2012| |
|
19/10/2012| |
|
19/10/2012| |
|
19/10/2012| |
|
19/10/2012| |
|
29/09/2012| |
|
10/09/2012| |
|
10/09/2012| |
|
10/09/2012| |
|
10/09/2012| |
|
10/09/2012| |
|
09/09/2012| |
|
01/09/2012| |
|
01/09/2012| |
|
01/09/2012| |
|
30/08/2012| |
|
24/08/2012| |
|
22/08/2012| |
|
22/08/2012| |
|
22/08/2012| |
|
21/08/2012| |
|
15/08/2012| |
|
15/08/2012| |
|
15/08/2012| |
|
13/08/2012| |
|
13/08/2012| |
|
10/08/2012| |
|
09/08/2012| |
|
09/08/2012| |
|
07/08/2012| |
|
06/08/2012| |
|
06/08/2012| |
|
06/08/2012| |
|
06/08/2012| |
|
31/07/2012| |
|
31/07/2012| |
|
31/07/2012| |
|
31/07/2012| |
|
28/07/2012| |
|
28/07/2012| |
|
28/07/2012| |
|
28/07/2012| |
|
28/07/2012| |
|
28/07/2012| |
|
28/07/2012| |
|
28/07/2012| |
|
25/07/2012| |
|
25/07/2012| |
|
15/07/2012| |
|
15/07/2012| |
|
14/07/2012| |
|
10/07/2012| |
|
10/07/2012| |
|
09/07/2012| |
|
14/06/2012| |
|
14/06/2012| |
|
09/06/2012| |
|
09/06/2012| |
|
09/06/2012| |
|
08/06/2012| |
|
04/06/2012| |
|
04/06/2012| |
|
03/06/2012| |
|
03/06/2012| |
|
21/05/2012| |
|
20/05/2012| |
|
20/05/2012| |
|
06/05/2012| |
|
27/04/2012| |
|
13/04/2012| |
|
13/04/2012| |
|
13/04/2012| |
|
12/04/2012| |
|
12/04/2012| |
|
07/04/2012| |
|
07/04/2012| |
|
06/04/2012| |
|
06/04/2012| |
|
04/04/2012| |
|
01/04/2012| |
|
01/04/2012| |
|
01/04/2012| |
|
19/03/2012| |
|
19/03/2012| |
|
18/03/2012| |
|
18/03/2012| |
|
12/03/2012| |
|
12/03/2012| |
|
04/03/2012| |
|
04/03/2012| |
|
04/03/2012| |
|
04/03/2012| |
|
04/03/2012| |
|
04/03/2012| |
|
04/03/2012| |
|
04/03/2012| |
|
02/03/2012| |
|
02/03/2012| |
|
02/03/2012| |
|
25/02/2012| |
|
25/02/2012| |
|
25/02/2012| |
|
25/02/2012| |
|
25/02/2012| |
|
25/02/2012| |
|
05/11/2011| |
|
30/10/2011| |
|
30/10/2011| |
|
29/10/2011| |
|
21/10/2011| |
|
11/10/2011| |
|
11/10/2011| |
|
08/10/2011| |
|
04/10/2011| |
|
03/10/2011| |
|
03/10/2011| |
|
03/10/2011| |
|
01/10/2011| |
|
01/10/2011| |
|
25/09/2011| |
|
24/09/2011| |
|
23/09/2011| |
|
23/09/2011| |
|
23/09/2011| |
|
23/09/2011| |
|
23/09/2011| |
|
20/09/2011| |
|
17/09/2011| |
|
17/09/2011| |
|
16/09/2011| |
|
15/09/2011| |
|
11/09/2011| |
|
11/09/2011| |
|
07/09/2011| |
|
07/09/2011| |
|
04/09/2011| |
|
04/09/2011| |
|
04/09/2011| |
|
04/09/2011| |
|
02/09/2011| |
|
02/09/2011| |
|
02/09/2011| |
|
02/09/2011| |
|
27/08/2011| |
|
27/08/2011| |
|
27/08/2011| |
|
27/08/2011| |
|
26/08/2011| |
|
26/08/2011| |
|
26/08/2011| |
|
26/08/2011| |
|
25/08/2011| |
|
25/08/2011| |
|
23/08/2011| |
|
23/08/2011| |
|
16/08/2011| |
|
16/08/2011| |
|
16/08/2011| |
|
16/08/2011| |
|
11/08/2011| |
|
11/08/2011| |
|
11/08/2011| |
|
07/08/2011| |
|
04/08/2011| |
|
29/07/2011| |
|
28/07/2011| |
|
24/07/2011| |
|
24/07/2011| |
|
23/07/2011| |
|
23/07/2011| |
|
22/07/2011| |
|
21/07/2011| |
|
21/07/2011| |
|
17/07/2011| |
|
17/07/2011| |
|
15/07/2011| |
|
15/07/2011| |
|
15/07/2011| |
|
15/07/2011| |
|
13/07/2011| |
|
13/07/2011| |
|
13/07/2011| |
|
13/07/2011| |
|
29/06/2011| |
|
29/06/2011| |
|
19/06/2011| |
|
19/06/2011| |
|
19/06/2011| |
|
19/06/2011| |
|
18/06/2011| |
|
18/06/2011| |
|
18/06/2011| |
|
18/06/2011| |
|
17/06/2011| |
|
17/06/2011| |
|
14/06/2011| |
|
14/06/2011| |
|
13/06/2011| |
|
13/06/2011| |
|
13/06/2011| |
|
13/06/2011| |
|
05/06/2011| |
|
05/06/2011| |
|
03/06/2011| |
|
03/06/2011| |
|
03/06/2011| |
|
03/06/2011| |
|
01/06/2011| |
|
01/06/2011| |
|
01/06/2011| |
|
01/06/2011| |
|
01/06/2011| |
|
01/06/2011| |
|
01/06/2011| |
|
01/06/2011| |
|
29/05/2011| |
|
29/05/2011| |
|
29/05/2011| |
|
29/05/2011| |
|
29/05/2011| |
|
29/05/2011| |
|
23/05/2011| |
|
23/05/2011| |
|
22/05/2011| |
|
22/05/2011| |
|
22/05/2011| |
|
22/05/2011| |
|
22/05/2011| |
|
22/05/2011| |
|
21/05/2011| |
|
21/05/2011| |
|
21/05/2011| |
|
21/05/2011| |
|
16/05/2011| |
|
16/05/2011| |
|
13/05/2011| |
|
13/05/2011| |
|
06/05/2011| |
|
06/05/2011| |
|
04/05/2011| |
|
04/05/2011| |
|
04/05/2011| |
|
04/05/2011| |
|
02/05/2011| |
|
02/05/2011| |
|
02/05/2011| |
|
02/05/2011| |
|
01/05/2011| |
|
01/05/2011| |
|
01/05/2011| |
|
01/05/2011| |
|
01/05/2011| |
|
01/05/2011| |
|
26/04/2011| |
|
26/04/2011| |
|
26/04/2011| |
|
26/04/2011| |
|
26/04/2011| |
|
26/04/2011| |
|
21/04/2011| |
|
21/04/2011| |
|
21/04/2011| |
|
21/04/2011| |
|
20/04/2011| |
|
20/04/2011| |
|
20/04/2011| |
|
20/04/2011| |
|
20/04/2011| |
|
20/04/2011| |
|
15/04/2011| |
|
11/04/2011| |
|
11/04/2011| |
|
08/04/2011| |
|
03/04/2011| |
|
27/03/2011| |
|
27/03/2011| |
|
26/03/2011| |
|
26/03/2011| |
|
20/03/2011| |
|
20/03/2011| |
|
19/03/2011| |
|
19/03/2011| |
|
19/03/2011| |
|
13/03/2011| |
|
13/03/2011| |
|
12/03/2011| |
|
11/03/2011| |
|
11/03/2011| |
|
09/03/2011| |
|
07/03/2011| |
|
07/03/2011| |
|
05/03/2011| |
|
04/03/2011| |
|
04/03/2011| |
|
04/03/2011| |
|
18/02/2011| |
|
21/01/2011| |
|
21/01/2011| |
|
16/01/2011| |
|
16/01/2011| |
|
11/01/2011| |
|
08/01/2011| |
|
02/01/2011| |
|
02/01/2011| |
|
29/12/2010| |
|
29/12/2010| |
|
28/12/2010| |
|
26/12/2010| |
|
13/12/2010| |
|
13/12/2010| |
|
08/12/2010| |
|
02/12/2010| |
|
30/11/2010| |
|
30/11/2010| |
|
28/11/2010| |
|
26/11/2010| |
|
26/11/2010| |
|
24/11/2010| |
|
16/11/2010| |
|
16/11/2010| |
|
16/11/2010| |
|
09/11/2010| |
|
07/11/2010| |
|
31/10/2010| |
|
31/10/2010| |
|
31/10/2010| |
|
26/10/2010| |
|
25/10/2010| |
|
22/10/2010| |
|
18/10/2010| |
|
16/10/2010| |
|
16/10/2010| |
|
11/10/2010| |
|
10/10/2010| |
|
10/10/2010| |
|
09/10/2010| |
|
05/10/2010| |
|
28/09/2010| |
|
28/09/2010| |
|
24/09/2010| |
|
24/09/2010| |
|
22/09/2010| |
|
22/09/2010| |
|
15/09/2010| |
|
15/09/2010| |
|
15/09/2010| |
|
12/09/2010| |
|
12/09/2010| |
|
12/09/2010| |
|
12/09/2010| |
|
06/09/2010| |
|
06/09/2010| |
|
05/09/2010| |
|
05/09/2010| |
|
29/08/2010| |
|
29/08/2010| |
|
29/08/2010| |
|
29/08/2010| |
|
22/08/2010| |
|
22/08/2010| |
|
21/08/2010| |
|
21/08/2010| |
|
21/08/2010| |
|
21/08/2010| |
|
21/08/2010| |
|
21/08/2010| |
|
14/08/2010| |
|
13/08/2010| |
|
13/08/2010| |
|
07/08/2010| |
|
07/08/2010| |
|
12/07/2010| |
|
12/06/2010| |
|
12/06/2010| |
|
12/06/2010| |
|
24/05/2010| |
|
24/05/2010| |
|
11/05/2010| |
|
10/05/2010| |
|
09/05/2010| |
|
09/05/2010| |
|
09/05/2010| |
|
01/04/2010| |
|
01/04/2010| |
|
31/03/2010| |
|
31/03/2010| |
|
31/03/2010| |
|
28/03/2010| |
|
28/03/2010| |
|
28/03/2010| |
|
20/03/2010| |
|
12/03/2010| |
|
12/03/2010| |
|
12/03/2010| |
|
08/03/2010| |
|
07/03/2010| |
|
06/03/2010| |
|
05/03/2010| |
|
03/03/2010| |
|
03/03/2010| |
|
28/02/2010| |
|
21/02/2010| |
|
19/02/2010| |
|
14/02/2010| |
|
11/02/2010| |
|
11/02/2010| |
|
10/02/2010| |
|
08/02/2010| |
|
08/02/2010| |
|
08/02/2010| |
|
28/01/2010| |
|
25/01/2010| |
|
20/01/2010| |
|
20/01/2010| |
|
16/01/2010| |
|
16/01/2010| |
|
15/01/2010| |
|
15/01/2010| |
|
11/01/2010| |
|
11/01/2010| |
|
10/01/2010| |
|
07/01/2010| |
|
03/01/2010| |
|
03/01/2010| |
|
03/01/2010| |
|
17/12/2009| |
|
15/12/2009| |
|
15/12/2009| |
|
13/12/2009| |
|
13/12/2009| |
|
28/11/2009| |
|
28/11/2009| |
|
28/11/2009| |
|
28/11/2009| |
|
27/11/2009| |
|
27/11/2009| |
|
27/11/2009| |
|
27/11/2009| |
|
27/11/2009| |
|
27/11/2009| |
|
21/11/2009| |
|
21/11/2009| |
|
18/11/2009| |
|
18/11/2009| |
|
16/11/2009| |
|
16/11/2009| |
|
30/10/2009| |
|
30/10/2009| |
|
11/10/2009| |
|
10/10/2009| |
|
10/10/2009| |
|
07/10/2009| |
|
07/10/2009| |
|
04/10/2009| |
|
30/09/2009| |
|
30/09/2009| |
|
27/09/2009| |
|
27/09/2009| |
|
27/09/2009| |
|
22/09/2009| |
|
20/09/2009| |
|
18/09/2009| |
|
18/09/2009| |
|
18/09/2009| |
|
16/09/2009| |
|
16/09/2009| |
|
16/09/2009| |
|
08/09/2009| |
|
07/09/2009| |
|
06/09/2009| |
|
06/09/2009| |
|
05/09/2009| |
|
05/09/2009| |
|
26/08/2009| |
|
21/08/2009| |
|
19/08/2009| |
|
19/08/2009| |
|
15/08/2009| |
|
15/08/2009| |
|
15/08/2009| |
|
11/08/2009| |
|
11/08/2009| |
|
11/08/2009| |
|
11/08/2009| |
|
19/07/2009| |
|
19/07/2009| |
|
18/07/2009| |
|
18/07/2009| |
|
27/03/2009| |
|
22/03/2009| |
|
22/03/2009| |
|
27/01/2009| |
|
27/01/2009| |
|
27/01/2009| |
|
17/01/2009| |
|
17/01/2009| |
|
17/01/2009| |
|
17/01/2009| |
|
17/01/2009| |
|
17/01/2009| |
|
11/01/2009| |
|
06/12/2008| |
|
06/12/2008| |
|
06/12/2008| |
|
06/12/2008| |
|
23/11/2008| |
|
23/11/2008| |
|
16/11/2008| |
|
16/11/2008| |
|
04/11/2008| |
|
04/11/2008| |
|
03/11/2008| |
|
03/11/2008| |
|
24/10/2008| |
|
24/10/2008| |
|
24/10/2008| |
|
24/10/2008| |
|
15/09/2008| |
|
15/09/2008| |
|
15/09/2008| |
|
15/09/2008| |
|
15/09/2008| |
|
15/09/2008| |
|
06/09/2008| |
|
06/09/2008| |
|
05/09/2008| |
|
05/09/2008| |
|
05/09/2008| |
|
05/09/2008| |
|
01/09/2008| |
|
01/09/2008| |
|
01/09/2008| |
|
01/09/2008| |
|
22/08/2008| |
|
22/08/2008| |
|
17/08/2008| |
|
17/08/2008| |
|
16/08/2008| |
|
16/08/2008| |
|
28/07/2008| |
|
28/07/2008| |
|
28/07/2008| |
|
28/07/2008| |
|
28/07/2008| |
|
28/07/2008| |
|
19/07/2008| |
|
19/07/2008| |
|
24/05/2008| |
|
24/05/2008| |
|
03/05/2008| |
|
03/05/2008| |
|
29/04/2008| |
|
11/02/2008| |
|
05/01/2008| |
|
09/12/2007| |
|
18/11/2007| |
|
10/11/2007| |
|
10/11/2007| |
|
06/11/2007| |
|
06/11/2007| |
|
06/09/2007| |
|
26/08/2007| |
|
25/08/2007| |
|
11/07/2007| |
|
16/06/2007| |
|
16/06/2007| |
|
10/06/2007| |
|
10/06/2007| |
|
19/05/2007| |
|
19/05/2007| |
|
19/05/2007| |
|
19/05/2007| |
|
24/04/2007| |
|
24/04/2007| |
|
14/04/2007| |
|
14/04/2007| |
|
05/04/2007| |
|
05/04/2007| |
|
05/04/2007| |
|
28/02/2007| |
|
28/02/2007| |
|
05/02/2007| |
|
05/02/2007| |
|
04/02/2007| |
|
04/02/2007| |
|
04/02/2007| |
|
04/02/2007| |
|
04/02/2007| |
|
04/02/2007| |
|
29/01/2007| |
|
29/01/2007| |
|
29/01/2007| |
|
29/01/2007| |
|
11/01/2007| |
|
11/01/2007| |
|
11/01/2007| |
|
11/01/2007| |
|
27/12/2006| |
|
27/12/2006| |
|
27/12/2006| |
|
27/12/2006| |
|
27/12/2006| |
|
27/12/2006| |
|
20/12/2006| |
|
20/12/2006| |
|
17/11/2006| |
|
30/09/2006| |
|
28/07/2006| |
|
12/04/2006| |
|
12/04/2006| |
|
12/04/2006| |
|
06/03/2006| |
|
21/02/2006| |
|
17/02/2006| |
|
31/01/2006| |
|
10/01/2006| |
|
28/12/2005| |
|
31/10/2005| |
|
26/09/2005| |
|
29/08/2005| |
|
11/08/2005| |
|
08/08/2005| |
|
24/06/2005| |
|
24/06/2005| |
|
24/06/2005| |
|
03/04/2005| |
|
03/04/2005| |
|
03/04/2005| |
|
03/04/2005| |
|